DARKMATTER LINK
The definitive verification gateway for the darkmatter market ecosystem. Establish a secure connection to the darkmatter darknet platform through our PGP-signed directory.
We provide a direct, encrypted bridge to verified darkmatter onion mirrors, ensuring you bypass imitation sites and connect directly to the official market infrastructure.
PGP VERIFIED
Cryptographic signature validation for every mirror link in our database.
DIRECT ROUTING
Official access points for the darkmatter market url with zero intermediation.
Primary Access
Authorized V3 Onion Address
VERIFIED MIRRORS
Redundant access nodes for the darkmatter darknet market. All links below are cryptographically verified daily against the platform's public key.
MIRROR_01
ONLINEvqsbd3smocn5xi4jv5he45545v7557xmnkixzuheg22go3pqnyf4roqd.onion
MIRROR_02
ONLINE3lfztlt4ehi2f4s7bojx72lb5vsnk6kcjpzynopzxdvg56rxb4q3mhad.onion
MIRROR_03
ONLINEph3h2vjnbxjl47gewgghtj2ni2tevo5to6dbtvvnlimutlzntz6jtoid.onion
Platform Interface
Secure. Utilitarian. Kali Linux Inspired Environment.
01_DDOS_GUARD
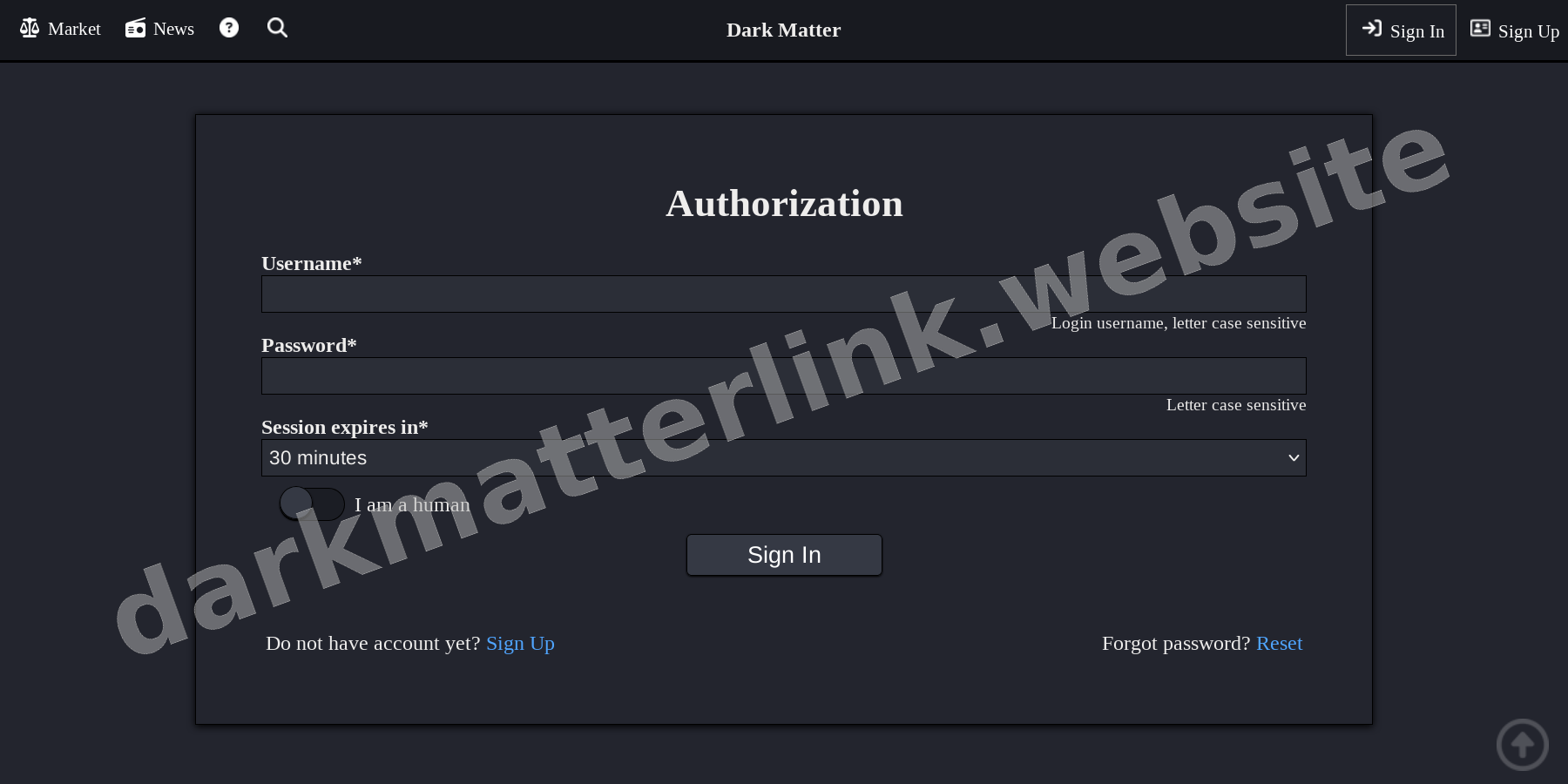
SYSTEM_ENTRY02_AUTH_GATE
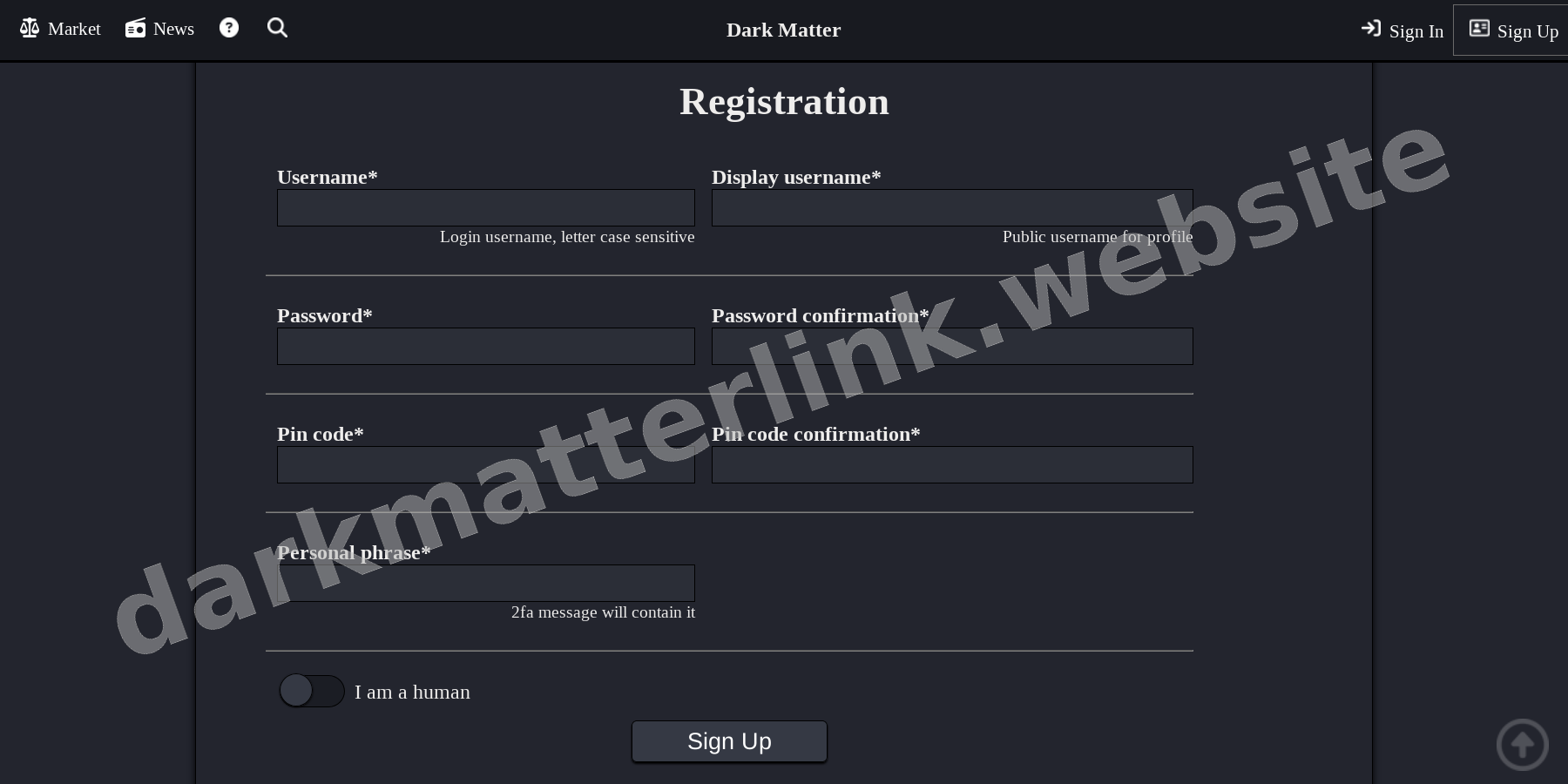
SECURE_LOGIN03_REGISTRATION
NEW_USER_PROTOCOL04_MARKET_CORE
MAIN_DASHBOARDOPERATIONAL INTEL
Darkmatter Market has established itself as a sovereign entity within the darknet ecosystem since its inception in 2023. Engineered with a decentralized server architecture, the platform maintains 99% uptime resilience against network attacks. With a user base exceeding 450,000 verified accounts, it stands as a pillar of reliability in a volatile landscape.
The platform enforces a strict Monero-only (XMR) policy, a deliberate architectural decision to ensure mathematical privacy for all financial interactions. Unlike Bitcoin-based markets where blockchain analysis can de-anonymize participants, darkmatter's implementation of Ring Signatures and Stealth Addresses provides a true zero-knowledge environment.
Security is not an afterthought but the foundation. From the mandatory PGP 2FA to the AI-assisted dispute resolution system, every feature is designed to protect user identity and funds. The market's interface, inspired by offensive security operating systems, reflects its utilitarian, no-nonsense approach to darknet commerce.
Decentralized Core
Distributed server nodes with automated failover systems ensure the darkmatter market link remains accessible during high-load events.
XMR Exclusive
Forced Monero adoption eliminates blockchain surveillance vectors, guaranteeing financial privacy for all generated invoices.
Neural Dispute System
Proprietary AI algorithms analyze transaction metrics to accelerate dispute resolution, reducing average case time by 65%.
Vendor Vetting
Strict 500.00 XMR bond requirement and multi-stage verification filter out low-quality merchants, ensuring a professional vendor pool.
Financial Protocol
Standard Operating Procedure for Account Funding
Acquire Asset
Purchase Monero (XMR) from a reputable exchange. Never send funds directly from a KYC-compliant exchange to a darknet market wallet.
Break Chain
Transfer purchased XMR to a private, local wallet you control (e.g., Monero GUI, Cake Wallet) to sever the link between your identity and the coins.
Generate Address
Access the darkmatter market wallet interface via the verified onion link. Generate a unique, one-time deposit subaddress.
Confirm Transfer
Send funds to the generated subaddress. The market requires 10 confirmations (approx. 20 minutes) before the balance becomes available.
PGP Encryption
Never rely solely on market-based auto-encryption. Always encrypt sensitive data (shipping info) locally using PGP before pasting it into the chat or order form. Import the vendor's public key and verify the fingerprint.
Link Verification
Impersonation is a constant threat. Only utilize links sourced from this verified repository or the official Dread sub-dread. Always verify the onion URL matches the PGP-signed message from the market administration.
OpSec Hygiene
Configure Tor Browser Security Level to "Safest" to disable JavaScript completely. Never reuse usernames or passwords across different markets. Use a dedicated OS like Tails or Whonix for maximum network isolation.
Access Protocol
Secure connection establishment procedure.
01 // ENVIRONMENT PREP
Before attempting connection, ensure your workstation is secure. We strongly recommend booting from a live USB operating system such as Tails OS. This ensures no data persists on your local hard drive and all traffic is forced through the Tor network by default.
02 // BROWSER CONFIG
Launch Tor Browser. Navigate to about:preferences#privacy or click the Shield icon. Set the Security Level to "Safest". This disables JavaScript globally, mitigating potential de-anonymization exploits and browser fingerprinting techniques.
03 // LINK ACQUISITION
Copy the primary darkmatter market onion link from the top of this page. These links are verified daily. Paste the V3 onion address into the URL bar. Wait for the circuit to build. If the connection times out, try one of the alternative mirrors listed in the Mirrors section.
04 // IDENTITY CREATION
Upon reaching the login gate, solve the captcha. Register a new account with a unique username not linked to other identities. Generate a high-entropy password (min 16 chars). Immediately navigate to settings and add your PGP public key to enable 2FA login protection.
Knowledge Base
Frequently Asked Questions regarding platform operations and security.
What is this portal?
This is a verified clearnet directory for the darkmatter-market. We provide PGP-signed .onion links to ensure users can locate the correct access points for the darknet platform without falling for impersonators.
What is a .onion link?
A .onion link is a specialized top-level domain designating a hidden service reachable via the Tor network. It offers end-to-end encryption and hides the server's IP address.
How do I access the market?
Download Tor Browser. Copy a verified link from our "Mirrors" section. Paste it into Tor Browser. Ensure your security settings are set to "Safest" (JavaScript disabled).
Is this the market itself?
No. This site is merely a signpost or directory. The actual market is hosted on the darknet. We provide the map to get there safely.
How are links verified?
Every link is checked against the market's official PGP key. Our automated scripts verify the signed message from the market admin every hour to ensure authenticity.
Why use this directory?
Navigating the darknet blindly is dangerous due to spoofed sites. This directory acts as a trusted anchor, ensuring you are routed to the legitimate infrastructure.
What is Tor Browser?
Tor Browser is a hardened web browser that routes traffic through three encrypted volunteer nodes, masking your IP address and allowing access to onion services.
Why only Monero (XMR)?
Bitcoin is transparent and traceable. Monero uses ring signatures to obfuscate sender, receiver, and amount. It is the only currency that guarantees financial privacy.
What is the vendor bond?
A 500.00 XMR deposit required for all new sellers. This high barrier to entry filters out scammers and ensures only professional vendors operate on the platform.
How do disputes work?
An AI system analyzes trade data to propose a resolution. A human moderator reviews this proposal. If the vendor is at fault, funds are returned to the buyer.
Is PGP mandatory?
Yes. Two-Factor Authentication (2FA) via PGP is required for all vendor accounts and strongly recommended for buyers to secure their wallets.
What is Auto-Finalize?
Orders automatically finalize after a set period (usually 7-14 days) if no dispute is raised. Ensure you check your order before this timer expires.
How to secure my wallet?
Enable 2FA. Never share your mnemonic seed. Withdraw funds immediately after a sale or refund. Do not leave excess XMR on the market wallet.
Can I use a VPN with Tor?
It is generally not recommended. Tor over VPN or VPN over Tor can introduce new risks. Standard Tor usage on Tails OS is the gold standard for OpSec.
What if a mirror is down?
DDoS attacks are common. If the main link is down, try the alternative mirrors listed above. They are hosted on different infrastructure to ensure redundancy.